Shodan - Treasure Hunting
December 30, 2019 - Reading time: 6 minutes
Today we will be discussing Shodan, a search engine for internet connected devices. I will be giving an overview of the filters you can use and the cool things that can be found with these filters.
As I mentioned Shodan (Link) is a search engine for internet connected devices, usually abbreviated as IOT devices. Shodan works by scanning the internet and processing the banners of the devices that reply to these scans, this is what Shodan looks like.
IOT devices are any devices that are connected to the internet, the device you are reading this on is an IOT device but things like smart fridges and industrial control systems can also be classified as IOT devices. I will be showing you how I use Shodan and the things it can be used to find.
But first a quick introduction to the filters it uses. You obviously do not want to to manually check each entry in Shodan to find what you are looking for, so you use filters. An example of a filter would look like this:
port:80 apache
This filter would return all the Apache web servers running on port 80, if I search with this I will get the following.
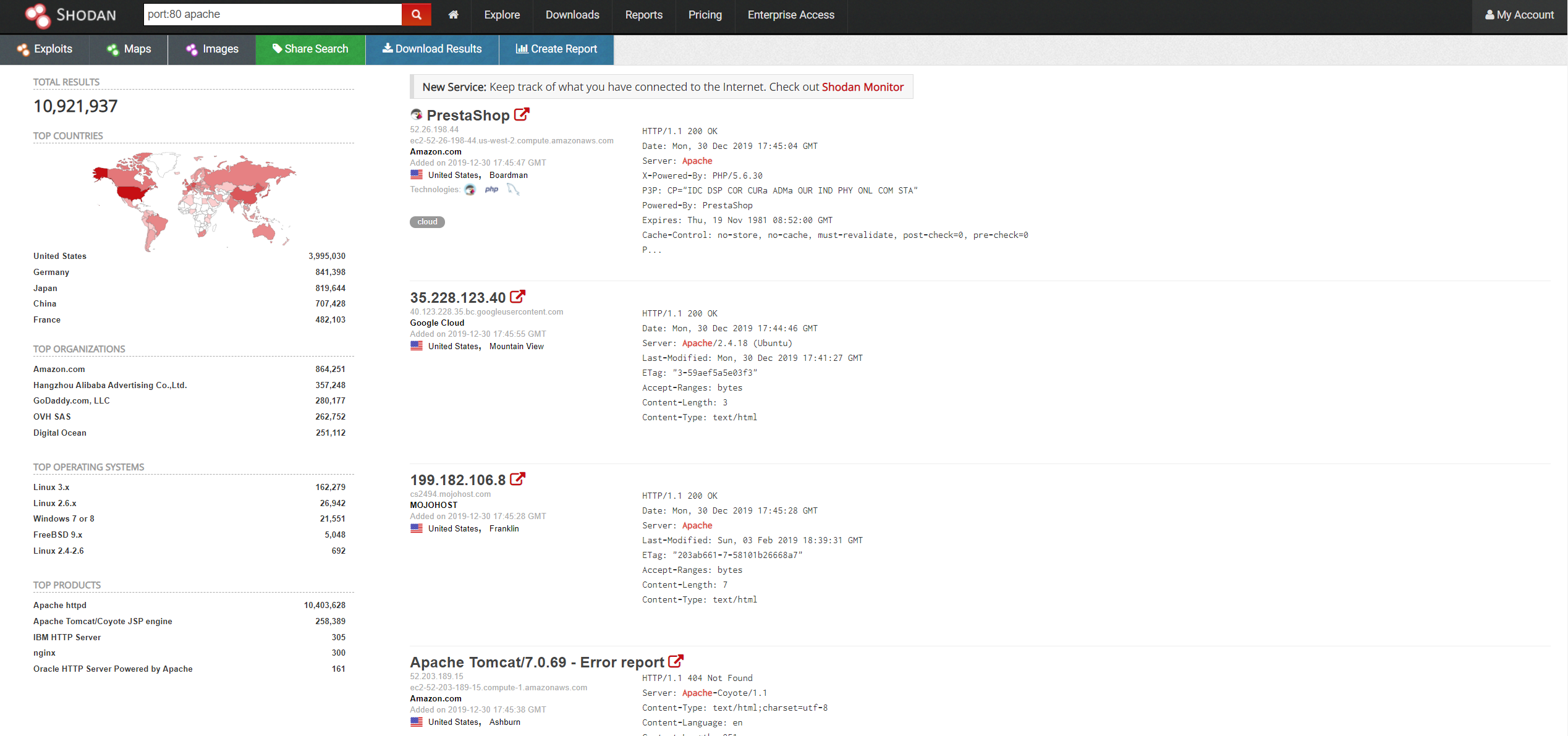
As you can see, I entered the search query in the top left and got close to 11 million results. Clearly this tool can be very powerful. I only needed to enter the port filter and the name of the software running. You will see more filters as I show some of the things that can be found. Search terms that are used in the security world are usually called "dorks", commonly used when referring to google search terms that expose sensitive data. The same word can be used here. I will now show you some of my favourite Shodan dorks.
The first is a dork that will expose many open CCTV cameras, these cameras are based all around the world and can be accessed relatively easily through your browser. The dork is:
title:"Live view"
When searching with the query we get the following.
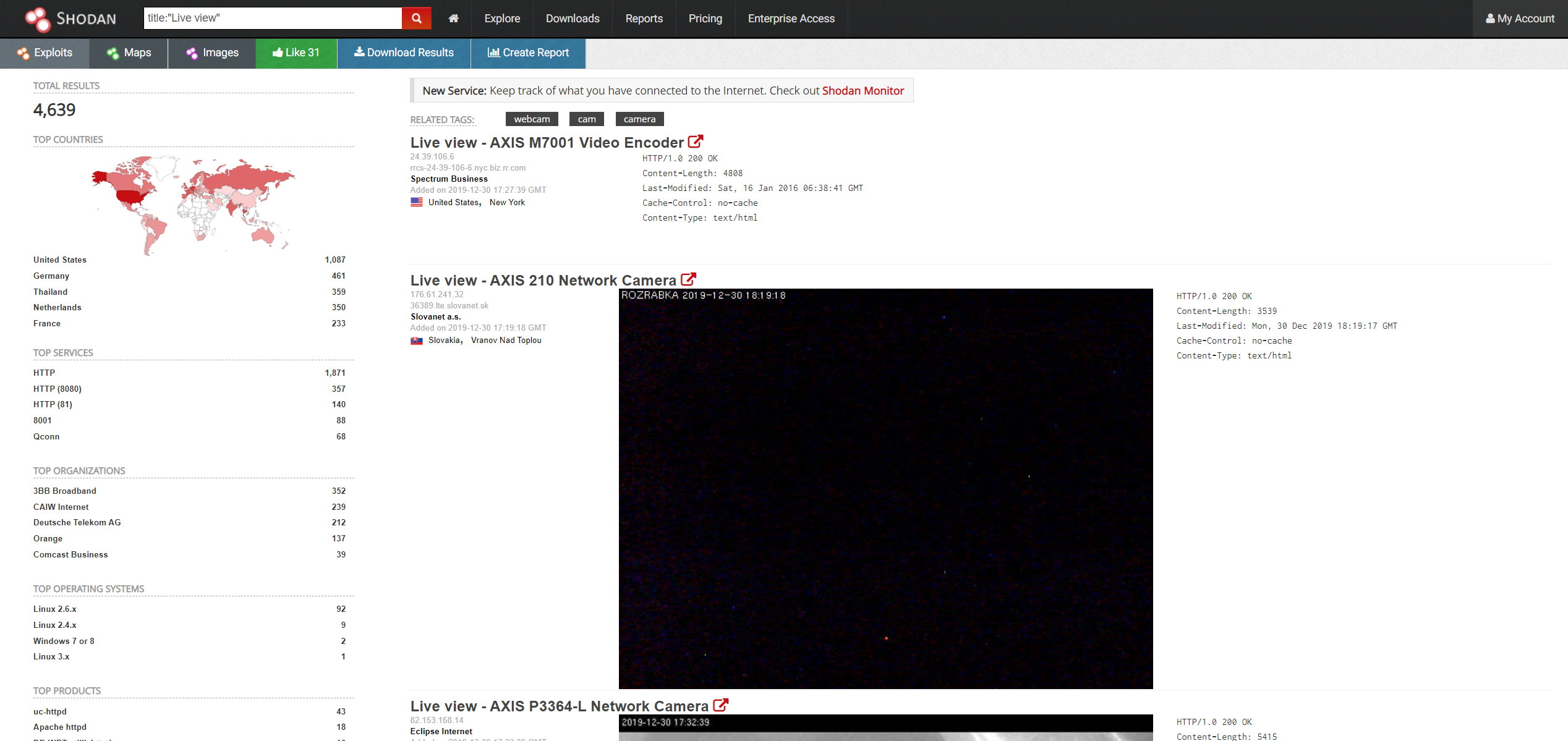
Shodan also provides images of some of its results. An example of this can be seen in the second entry, this is a screenshot of one of the outputs of a CCTV camera. This specific dork usually turns up results from AXIS brand cameras. Here is a screenshot of one of the entries.
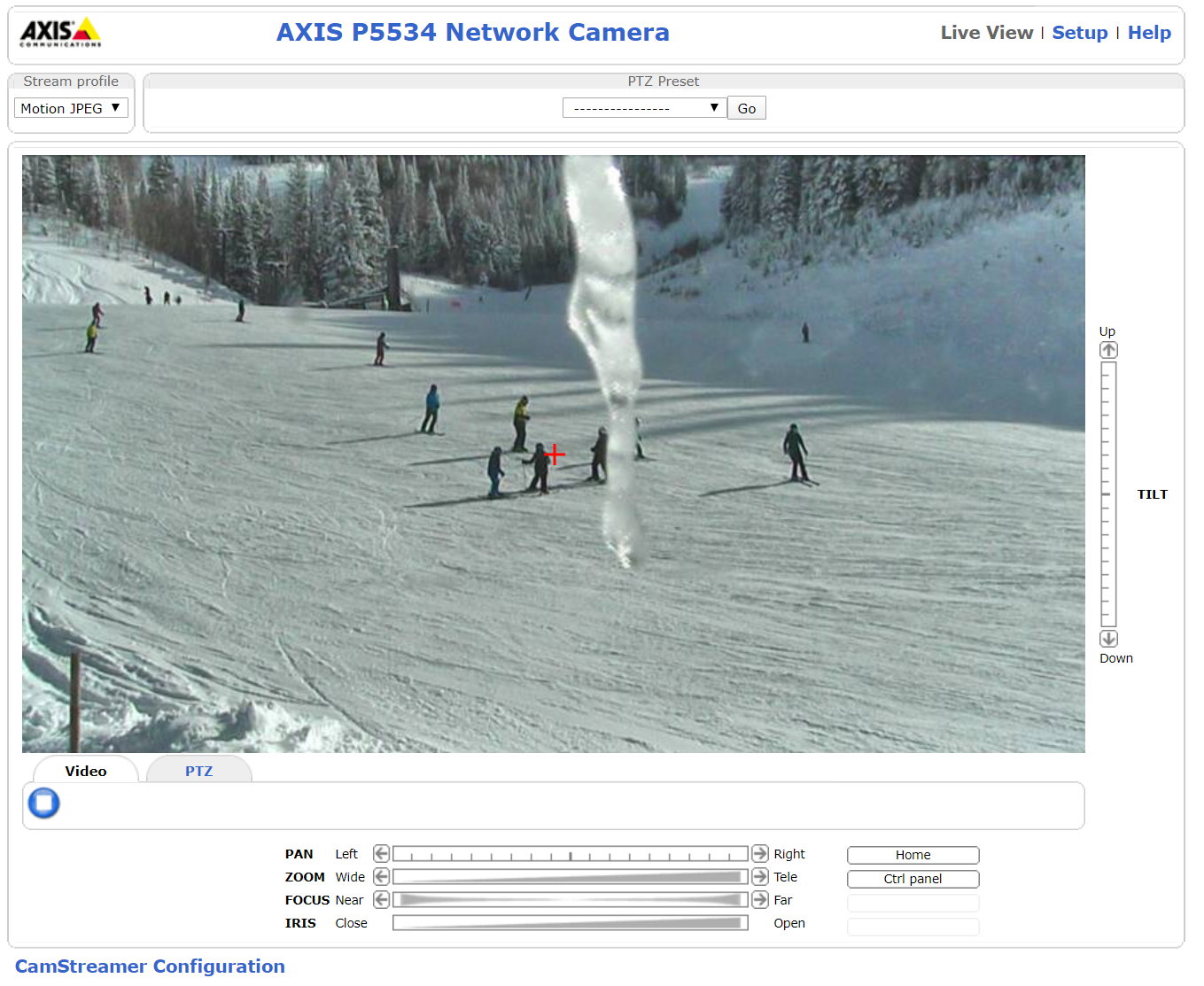 This is a ski slope somewhere in America and is an example of the things you can see through these cameras. But I wish all these cameras were pointing at nature as there are many that are in peoples houses, I will not show images of these but please believe me that they exist.
This is a ski slope somewhere in America and is an example of the things you can see through these cameras. But I wish all these cameras were pointing at nature as there are many that are in peoples houses, I will not show images of these but please believe me that they exist.
Now onto more security related things. You can also find peoples hacking tools uploaded for anyone on the internet to see. Spammers use tools called "Mailers" that are pieces of code that will email a list of emails with their desired content. These are usually used to spread malware or other unwanted scams. Here is a dork that can find these mailers:
http.title:"Priv8 Mailer"
As you can see, we are searching the title of http web servers for the string "Priv8 Mailer". Here is the results page when I carry out such a search.
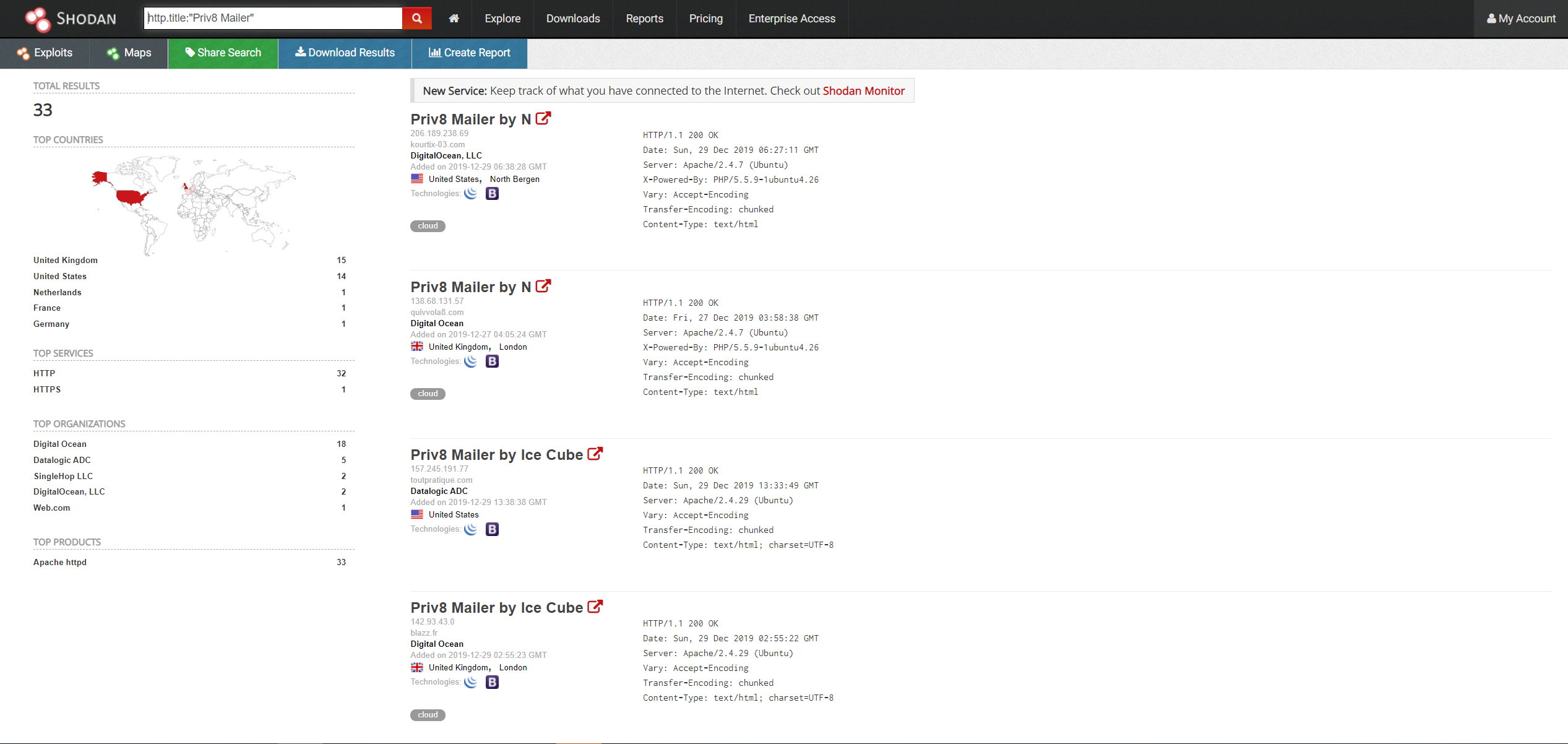
And if we visit one of these entries:
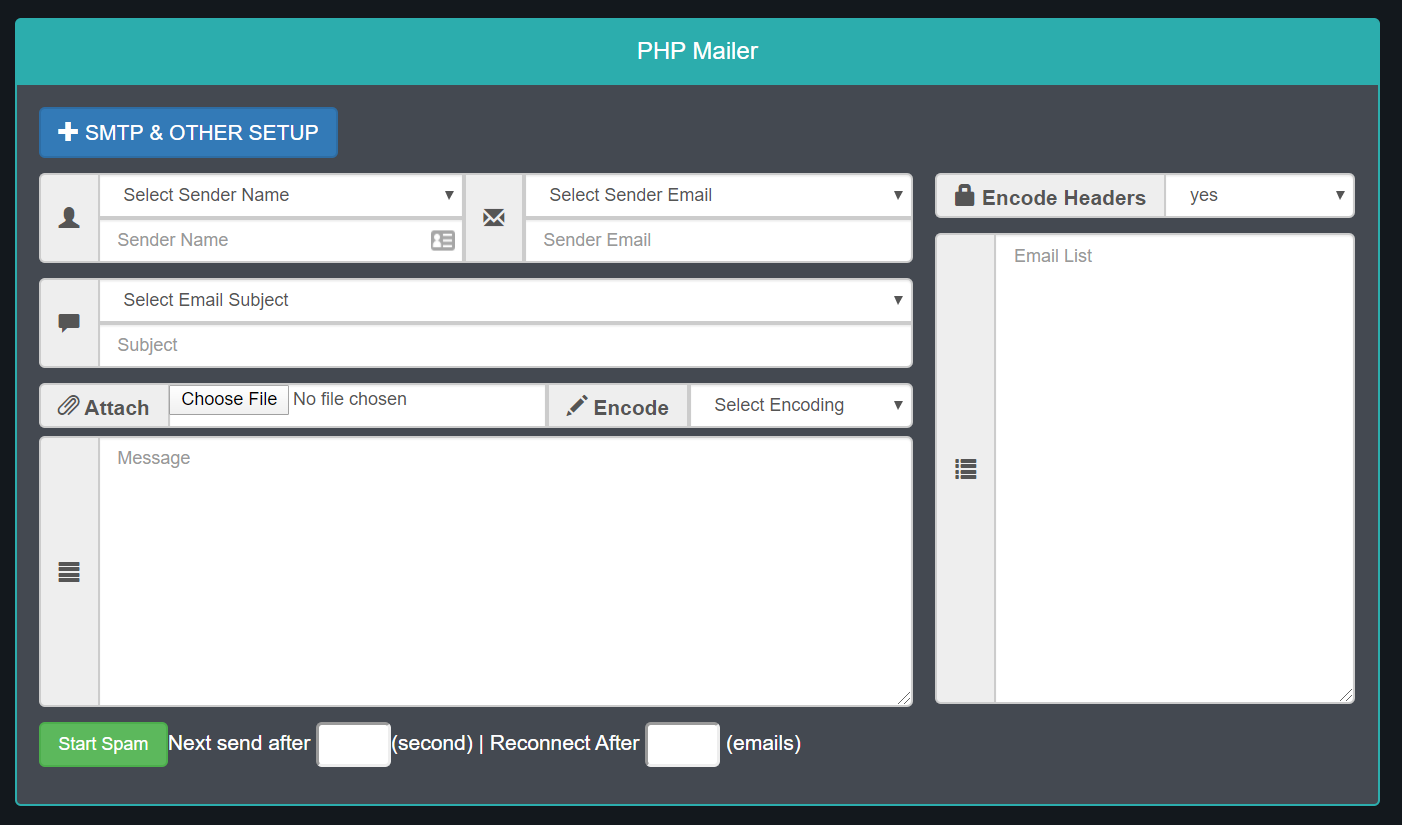 We can see the php mailer itself.
We can see the php mailer itself.
The last thing I want to show is how Shodan also indexes game servers. The game that I found most interesting to search about with Shodan is Minecraft. Minecraft allows users to create their own servers running on port 25565. I will use the same technique I used in the intro where I query using the port filter. The dork looks like this:
port: 25565
And returns this.
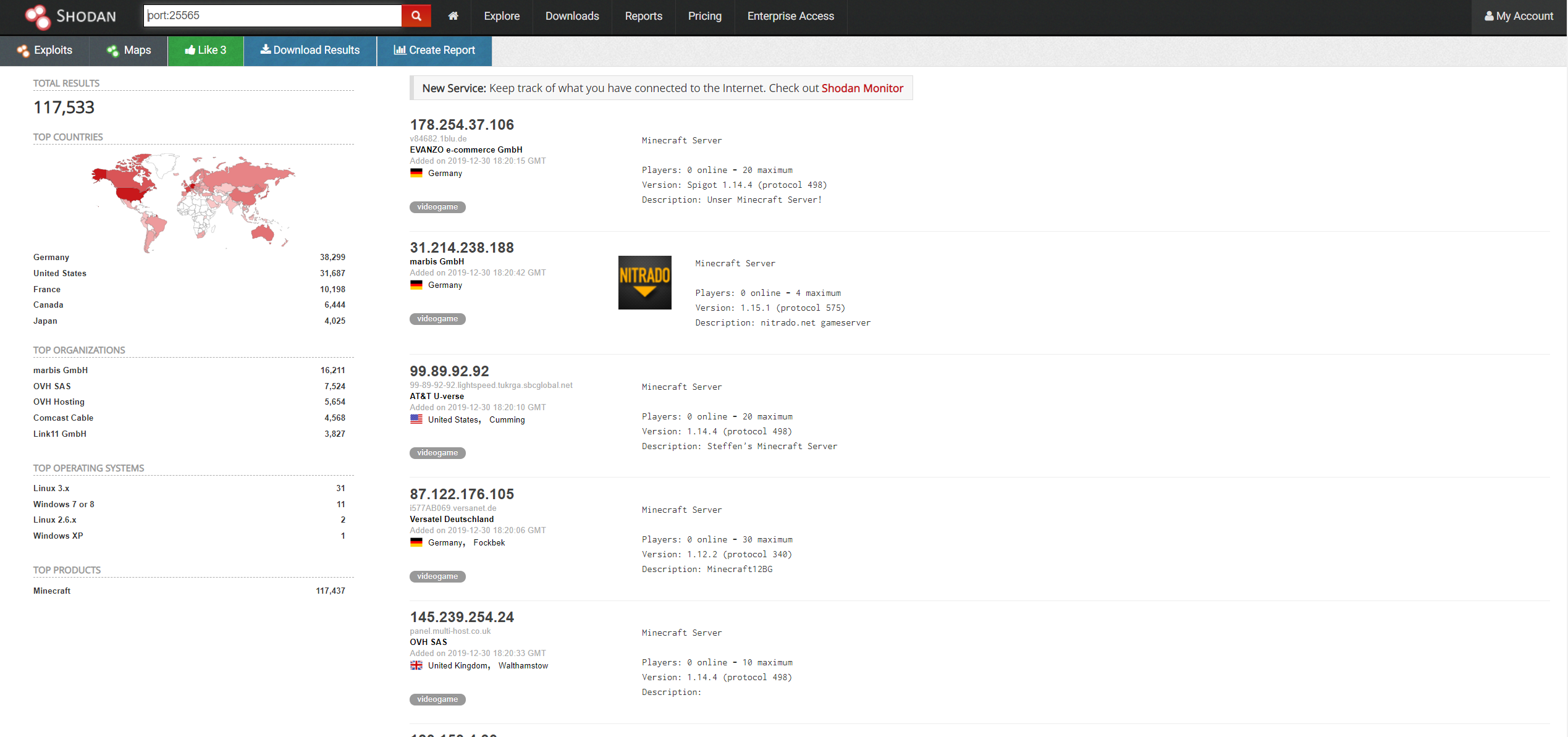
As shown there are close to 120k individual Minecraft servers that are indexed by Shodan. Since Shodan works by reading banners we can also see specifics about the servers like how many players are playing and what version of the game it is running.
I hope that you can see the potential Shodan has and how powerful of an OSINT (Open source intelligence) tool it can be. It also shows the flaws in security of some devices an example being how I could access CCTV cameras with relative ease, you should be mindful of the things you leave open to the internet and the potential damage that it can cause. Until the next time, have a good day!