TumblerCC - How not to run a scam
December 15, 2019 - Reading time: 5 minutes
This is a story about how I came across a credit card store that turned out to be a complete facade and how I exploited it to find more information about the site and what allowed me to take advantage of these flaws.
I spend a lot of time on Shodan (Link). For those of you that do not know what Shodan is, it's a search engine for IOT (internet of things) devices. These are devices that are connected to the internet ranging from normal computers to smart fridges. I will probably make a separate post about Shodan and the things I have found through it. As I was searching around for credit card stores I came across something called TumblerCC and decided to explore further.
Here is what TumblerCC looks like from the outside:
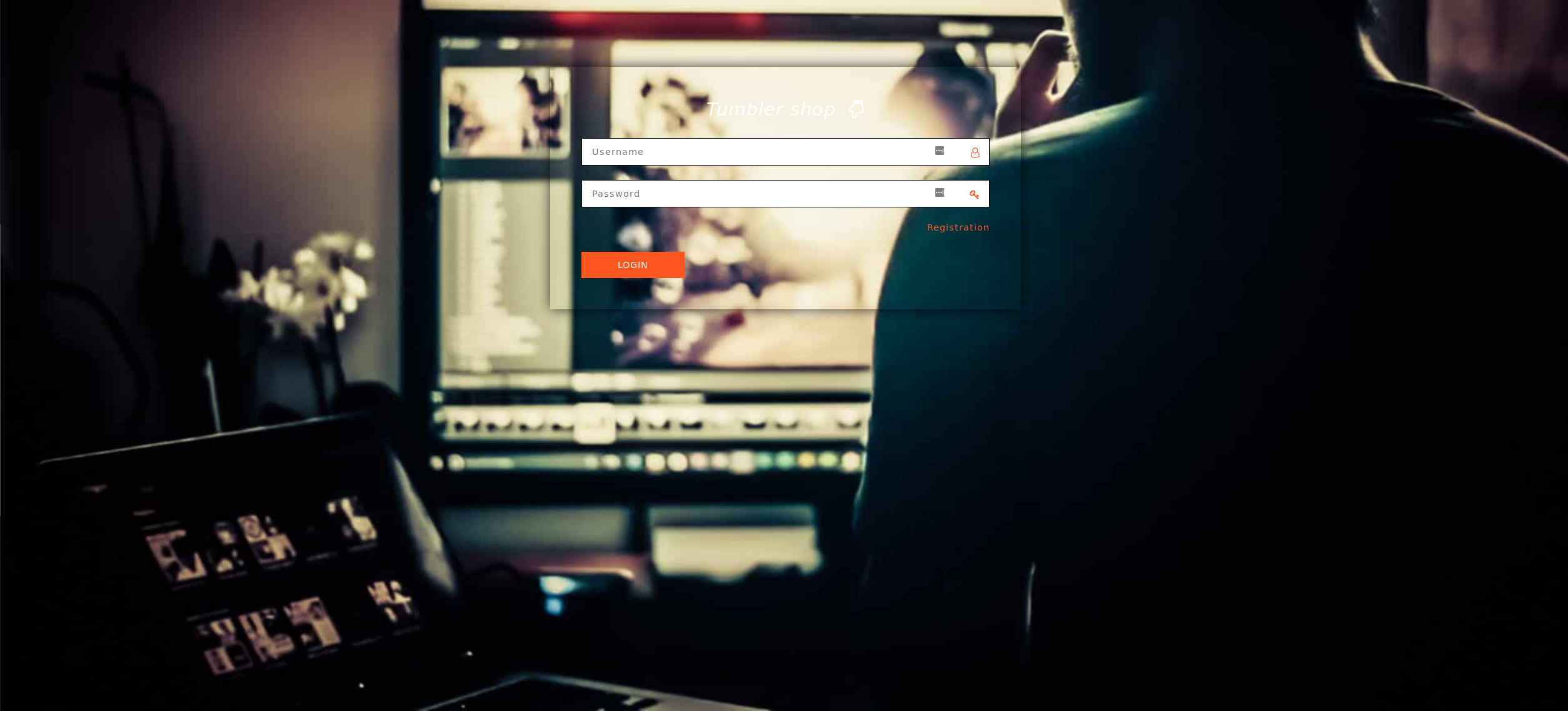
Although it is hard to see, it does say "Tumbler Shop" above the login form and to the bottom right there is a prompt to register. After registering I went on to look at what the site looked like from the inside:
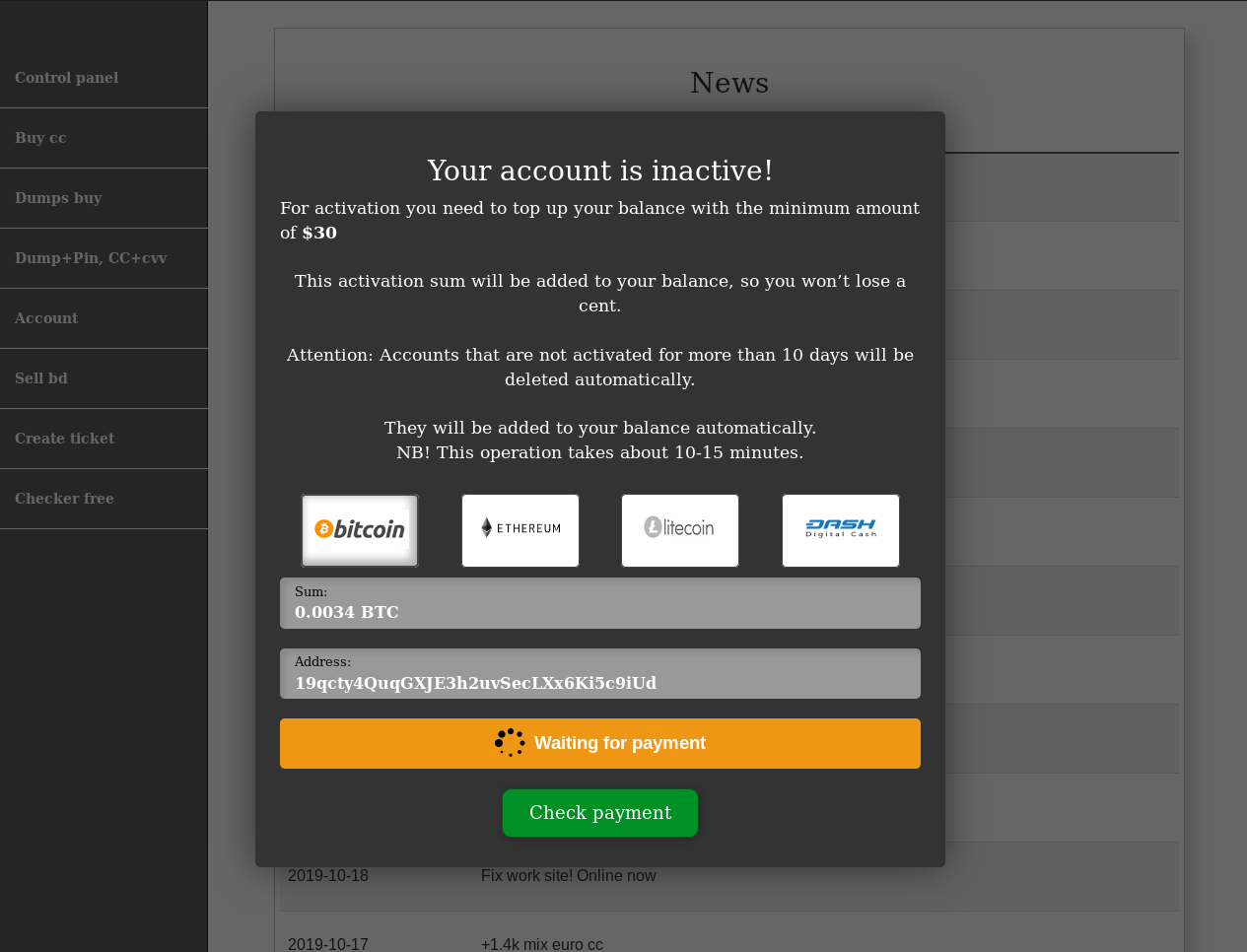
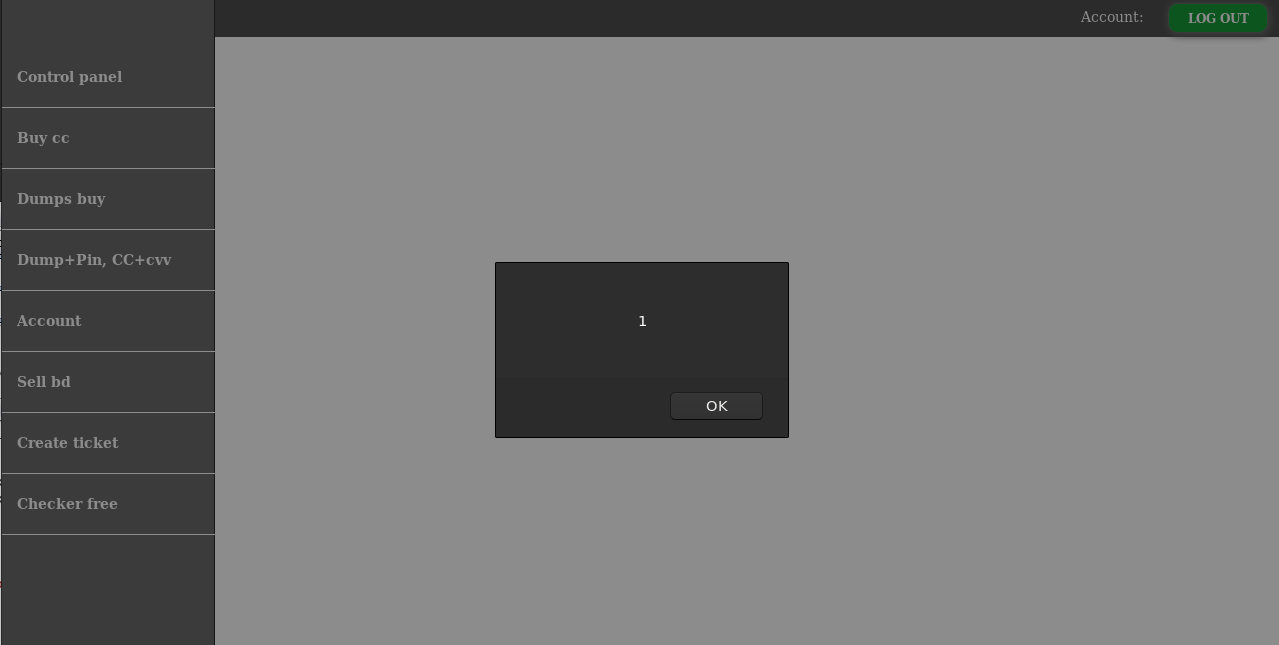
Upon login you are met with this popup, to the unfamiliar it looks like a registry fee but when I saw this I knew that the site was a scam. Due to this popup always being in front of the screen I used some inspect element magic to remove it. Here is what the site behind it looks like:
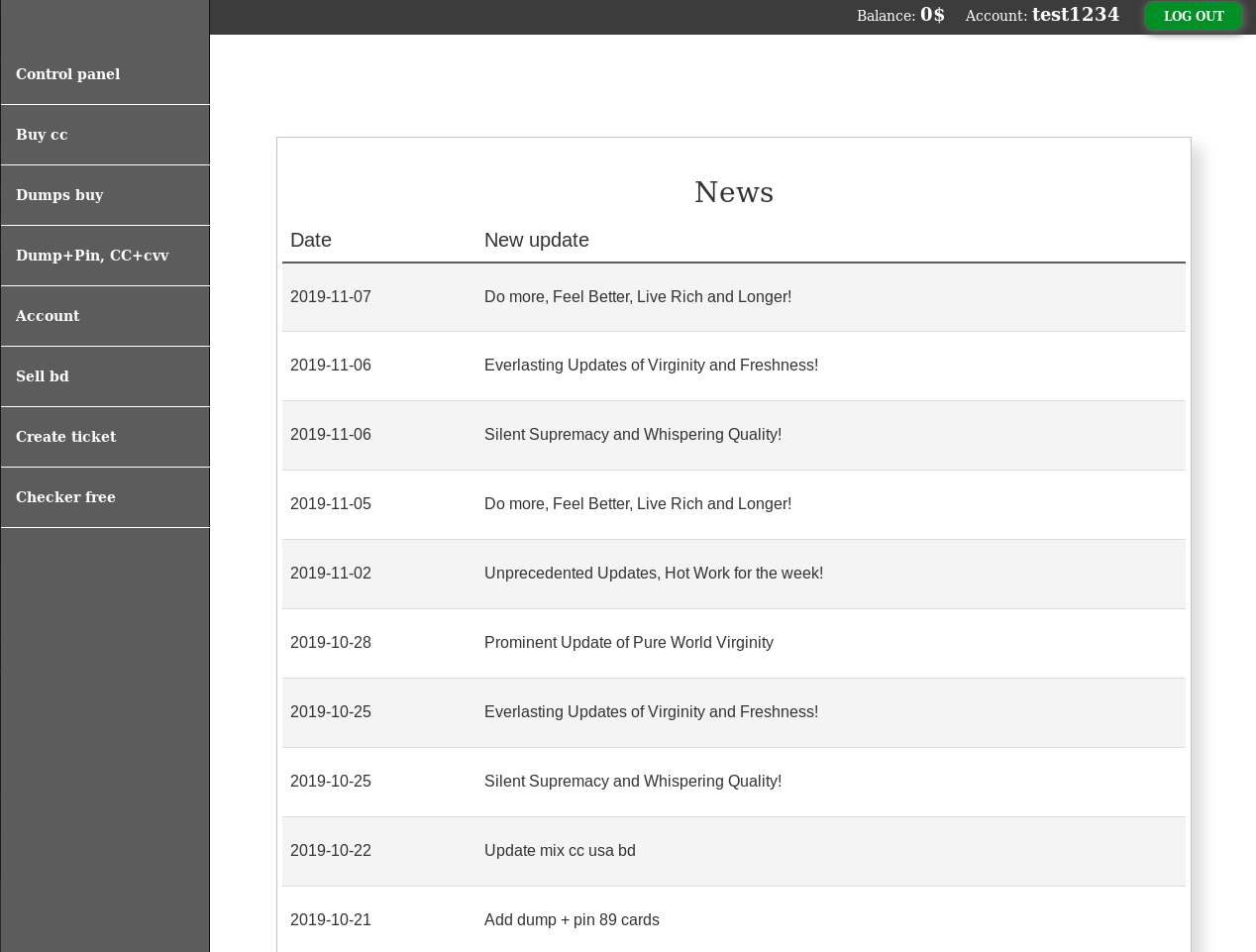
A very normal looking credit card shop, complete with purchasing pages, account, support tickets and card checker. Everything you would expect from a generic credit card store except for one issue. None of these were clickable and if I wasn't certain that this was a scam then this would be undoubtable evidence.
So now that I knew exactly what I was dealing with I got to work trying to find a way to exploit it. Upon registering, a few cookies are set in the browser and you are sent back to the index page. This request looks like so:
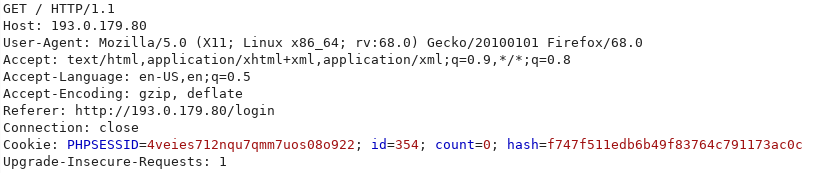
To the keen eyed of you, you will see that there is a cookie set with an id that is assigned to a small number. For those that have played around with web exploitation before you would know that this is commonly an iterating number that is assigned to your account upon registering, it is probably not wise to allow the user to see this. What's worse about this is that it is not checked, which means that if you change this number and resend the request, you will have access to someone else's account (Jackpot). So to exploit this I simply set up an intruder in burp to iterate between 0 and 10000 to see what would change. After realising that this would display the username of the logged in user I added a grabber to get these usernames:
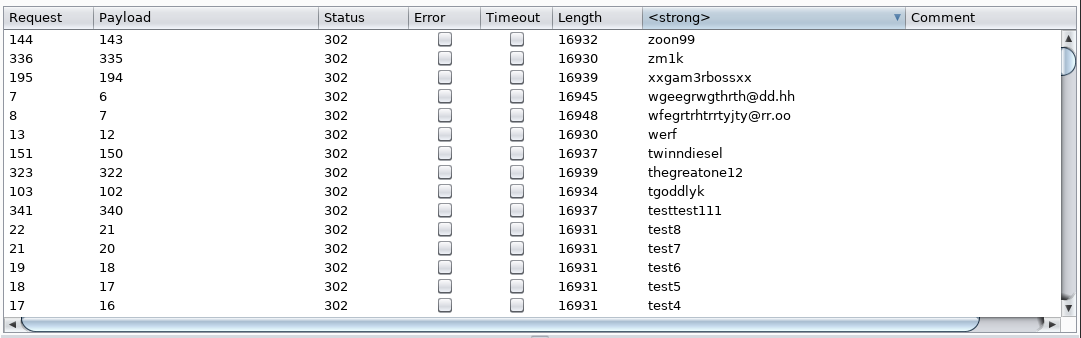
This is really the extent of what I can do with this exploit and I will add a link to all the users at the end of this post. After this I went on to check if there was xss in the registration. Of course there was:
But after discovering this, it was obvious that there would be no real use to it due to the nature of the site. I went on to try other exploits but discovered nothing, I did discover an admin page but that didn't result in much at all.
That about sums it up for my first post and I hope that you enjoyed the read. This didn't really amount to anything but it was fun playing around with the site. Hopefully you learnt something about site security. Here is some information about what I found:
Crypto Addresses:
- BTC: 14Ynp6DPccDxQAy4UVPkNTTYPCEVivWH3A
- ETH: 0x796d02aB720fDD49F6b39A2DDaea8EBD7793C30a
- LTC: MWmd3qqf6FU8irx1MemUfHRBZWWfZo9wRb
- DASH: XhYKA1LygD3jSALKT12xwsiZUNtS1wT4Ui
Payments To Addresses:
- BTC: 3 Succesful 30$ payments, most recent - 03/11/2019
- ETH: None
- LTC: None
- DASH: None
User list: